Cloud native EDA tools & pre-optimized hardware platforms
Building Trust in IoT from the MCU
Billions of devices are being connected to the Internet of Things (IoT), while the number of attacks on these devices is increasing rapidly. If data is considered the currency of the IoT, that currency has value only if the data comes from a trustworthy source and is untampered. As such, data integrity has a direct impact on business and infrastructure. We need to look at embedded microcontrollers (MCU), the orchestrating components in all these devices, to reduce the number of attacks. MCUs need to ensure security for IoT data at rest and in motion and protect the IP that operates the device. But how can an MCU vendor create a scalable security solution under extreme price pressure in a market? MCU vendors can differentiate in a competitive market with a fit-for-purpose security solution.
Problem
- Since valuable data is being generated in the billions of deployed edge devices, IoT security needs to start from the edge
- For creating trustworthy data and security for IoT?devices, a strong identity is required
- Traditional ways of creating and storing keys that form a device identity are too costly, not reliable, and not flexible enough for high volumes of IoT

Solution
- Start security where the data is created by deriving a unique and unclonable identity for every device
- Use an?SRAM PUF?to create an unclonable identity that authenticates the source, ensures data integrity, and protects valuable IP
Results
- An unclonable, immutable, invisible, and unique identity to authenticate every device
- Secure, authenticated data from the moment it is created, delivering end-to-end protection
- Best-in-class combination of high security, low costs, and high flexibility for IoT security
- Read/Modify protection for secret root key
- Protection?for hardware and software from misuse and counterfeiting
Strong security functions are needed on every device to protect the IoT from its enormous attack threat. Functions such as authentication, secure boot, IP protection, secure communication, and software updates are needed to protect devices. However, IoT devices have considerable constraints. Chips need to be small in size, operate at high speed with low power consumption, and cost effective. How can strong security be deployed under these constraints?
Strong Authentication
Authentication and security start with an unclonable device identity. All security functions require cryptographic keys derived from this identity, making the identity the root of all security. The keys authenticate the device and its data and encrypt data at rest and in transit.
How do the identity and keys get on a device’s MCU, and how are they stored securely? Through 草榴社区' SRAM PUF technology. SRAM PUFs create an unclonable, device-unique key from tiny variations in silicon. This key is never stored and cannot be copied. It is immutable and invisible to attackers, creating an unparalleled trust anchor.
SRAM PUF keys are the basis for IoT security:
- Device authentication: PKI-based handshake for secure communication
- Data confidentiality: encrypt sensitive data and keys, preventing data extraction from the device and reverse engineering of valuable IP
- Data integrity: protect against tampering and theft with the signing of device-specific firmware

SRAM PUF Availability
草榴社区 provides its SRAM PUF solutions both as IP and as software for embedding in an MCU or integrating into its firmware. The solution has a small footprint and, most importantly, a cost amenable to profitable scaling of the IoT. Algorithms for symmetric and public key cryptography are included and compliant with NIST specifications. SRAM PUFs scale over all popular fabs and process nodes, and SRAM is universally available in all MCUs.
- Network Connectivity: Authentication and encryption to protect communication & data
- IP Protection: Signing and encrypting IP with device-unique SRAM PUF keys to prevent reverse-engineering & device counterfeiting
- Consumable Connectivity: Authentication protocols to allow monitoring of consumables
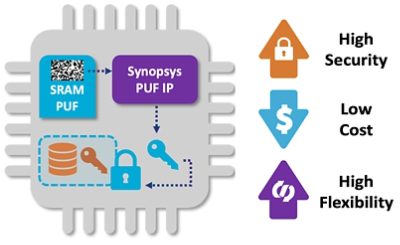
Bottom Line Benefits
- Unclonable, immutable and invisible identity
- Device authentication and data integrity
- Best-in-class combination of high security, low costs, and high flexibility for IoT security
- Secure storage for all keys and data
- Protection for hardware and software from overproduction and counterfeiting





